#
Category: red-team
See all categories.
red-team
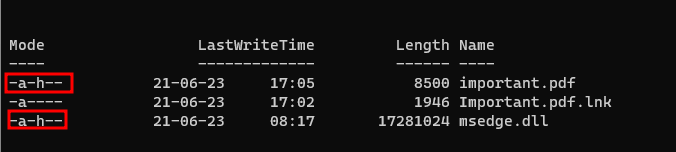
How to weaponize USB key like a real script kiddy for fun & profit
During a red team engagement, it can be interesting to learn how to weaponize a USB key (all in full storage) to gain initial access.
2023-08-03

red-team
How to protect your C2 (or Yes, an another Red Team infrastructure blog)
Hi everyone, it's been a while since my last blog post.
2025-06-08